Cybersecurity is a constantly evolving field, one in which being vigilant and prepared is vital to protecting our information systems. In this chapter, we’ll explore the basics of cyber threat intelligence, a crucial skill for staying ahead of digital threats.
But first, what exactly is cyber threat intelligence?
Think of it as a sentry keeping a watchful eye on the technological and business environment, identifying potential threats and opportunities to stay ahead of new developments.
If you’d prefer a more formal definition, NIST (U.S. National Institute of Standards and Technology) describes threat intelligence as:
“threat information that has been aggregated, transformed, analyzed, interpreted, or enriched to provide the necessary context for decision-making processes.”
Understand the Importance of Cyber Threat Intelligence
Cyber threat intelligence is both a process and an activity that all security professionals need to carry out. It can even be a job in its own right!
Cyber threat intelligence must be carried out continuously and be structured around a cyclical process. In this sense, it is similar to the intelligence cycle, which is a systematic process of collecting, analyzing, producing, and disseminating information of interest to an organization, company, or professional.
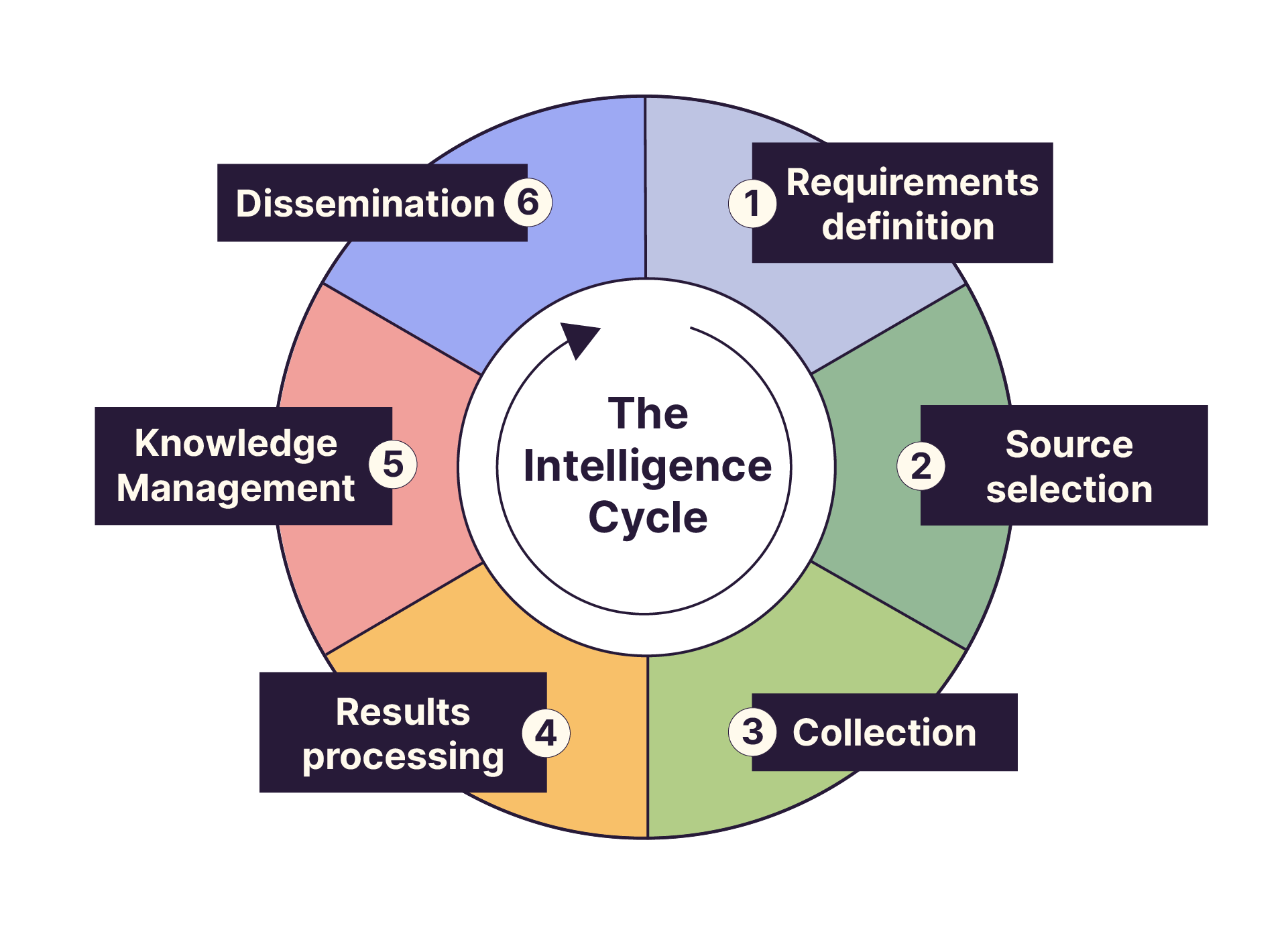
Implementing this process is vital if we want to respond effectively to mounting threats and an ever-changing regulatory framework. The demand for cyber threat intelligence is growing within organizations, making it an integral part of how we protect information systems and manage the flow of information on cyber risks.
But why is cyber threat intelligence so important?
Cyber threat intelligence is vital for ensuring that security professionals stay well-informed about cyber threats and risks.
It plays an integral part in a company’s information systems (IS) protection strategy (e.g., defining and managing security strategies).
Responding effectively and appropriately to cyber incidents is a must.
Cyber threat intelligence is essential because of the constantly evolving nature of technology. Rapid technological advances create new attack vectors and vulnerabilities.
What’s more, threat intelligence is intrinsically linked to the highly dynamic nature of geopolitical events, which can have a major impact on digital security.
Be Aware of the Unique Features of Cyber Threat Intelligence
Cyber threat intelligence differs from other fields in several ways. Firstly, the flow of information is exponential. It is therefore crucial that your threat intelligence is consistent and effective, rather than exhaustive.
Secondly, this information often has a limited lifespan. Cyber threats and vulnerabilities evolve rapidly, so you need to work quickly when gathering information.
This information may also be subject to strict rules on sharing and use.
Explore the Different Categories of Cyber Threat Intelligence
Cyber threat intelligence has many facets but will typically focus on specific aspects depending on the type of information you’re looking for. Broadly speaking, the categories include the following:
Threat detection involves monitoring malicious cyber activities that could compromise an organization.
Risk monitoring focuses on an organization’s attack surface to identify potential vulnerabilities.
Geopolitical intelligence monitors political and economic developments to predict their impact on an organization.
Competitive and ecosystem intelligence provides insights into the activities of competitors and partners so companies can keep pace with the cyber maturity of their competitors and partners and remain competitive and responsive in a constantly changing environment.
Regulatory and legal monitoring helps ensure compliance with ever-changing laws and regulations.
Technology trend monitoring focuses on technological advances in a particular field, to keep abreast of innovations and opportunities that could have an impact on a company’s business.
Lastly, reputation monitoring keeps a close eye on a company’s reputation and visibility so it can react quickly to any crisis.
Understand the Prerequisites of Cyber Threat Intelligence
Curiosity and Patience
Be curious and remember that threat intelligence takes time and patience. The skills you develop are vital to keeping your organization secure.
Information Search and Sorting
To be effective, you need to know how to search for and sort relevant information. Knowing how to use the advanced features of search engines and threat intelligence tools is crucial. We’ll come back to tips and best practices a little later.
Access to Threat Intelligence Tools
To automate and simplify your threat intelligence, you may need tools for collecting, analyzing, and monitoring data specific to cybersecurity. I’ll share some of these with you in the second part of the course.
Technical Expertise
Those who need to carry out active operational threat intelligence and in-depth analysis of cyber threats may require technical expertise.
Language Skills
Last but not least, language skills are a major asset. Although the vast majority of sources on cybersecurity are in English, a knowledge of other languages such as Russian, Chinese, Arabic, or Persian may be relevant to your threat intelligence.
Let’s Recap!
Cyber threat intelligence is a proactive, continuous, and cyclical process.
It’s vital for preempting threats and keeping abreast of changes in the regulatory framework.
Cyber threat intelligence is unique because of the huge flow of information, the speed of change, and specific rules on sharing information.
There are many different categories of cyber threat intelligence, including threats, risks, geopolitics, competition, ecosystem, regulations, technology, and reputation, all of which are vital for making informed decisions and staying competitive.
Cyber threat intelligence requires time, curiosity, and perseverance.
Skills in relevant languages and in research tools are essential.
In the next chapter, we’ll look at how you can structure your cyber threat intelligence around your specific goals.
