You now know more about the different types of cyber threat intelligence. They are vital for making informed decisions and staying competitive in a constantly changing world. These different types of threat intelligence all address an organization’s specific operational, tactical, and strategic goals.
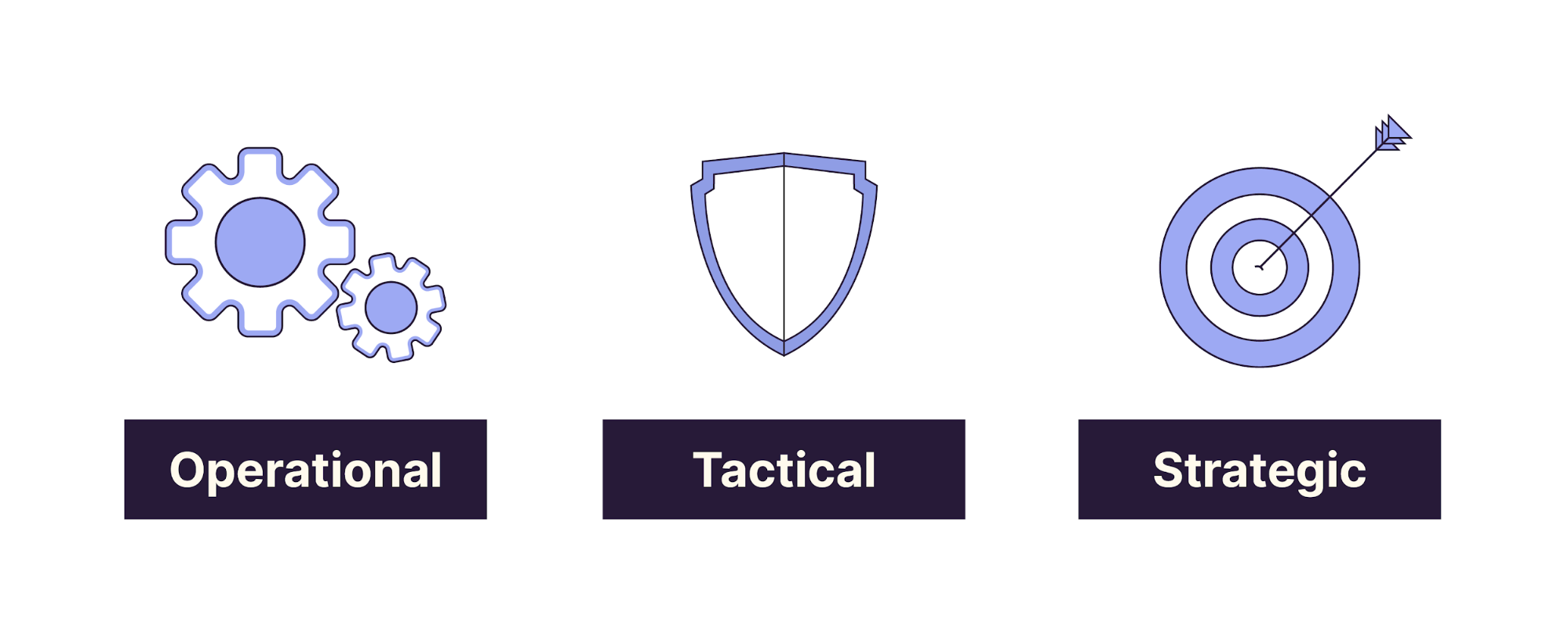
The use of threat intelligence is key at each of these three levels. This is because the collection and analysis processes are likely to determine how an organization allocates resources, presents information to decision makers, and so on. We will return to these levels throughout the course.
List Your Operational Goals
Operational threat intelligence aims to help security professionals manage the operational side of their organization’s systems and data. It helps organizations to:
identify abnormal behavior: Early detection of unusual behavior on a computer network is vital for early warning of possible intrusion or malicious activity. Intrusion detection systems, log analysis, and network traffic monitoring tools are essential for spotting these weak signals.
detect security incidents: Cyber threat intelligence looks for signs of successful intrusion or compromise (breach) of information systems so that organizations can respond quickly.
respond quickly and effectively to exploited vulnerabilities: Threats are constantly evolving, with attackers discovering and exploiting new vulnerabilities all the time.
Organizations can strengthen their security posture and protect their digital assets by implementing proactive detection, compromise identification, risk assessment, and rapid response processes.
Actively monitoring for new indicators of compromise associated with active malware means you can use these same indicators to check whether the associated threat is present on your network. If it is, you can prevent an intrusion—or detect a successful intrusion—sooner rather than later.
List Your Tactical Goals
Tactical threat intelligence helps companies understand the nature of known and emerging cyber threats so they can strengthen their security posture. It helps organizations to:
collect the information they need to identify cyber risks.
improve their knowledge of threat actors’ modus operandi (techniques, tools, etc.).
adjust their defense mechanisms to adapt to known and emerging threats (threat actors, malicious tools used, recognized attack techniques).
identify additional protection measures they may need to implement.
Let’s imagine a group of attackers known to target your industry. If you know about changes in the way they operate, you can more effectively manage the risks your organization is exposed to. Any change in their initial access tactics aimed at exploiting vulnerabilities in a specific software program is likely to lead to tighter security measures around how you manage that software.
List Your Strategic Goals
Strategic threat intelligence focuses on a series of goals aimed at understanding the motives and intentions of attackers, contextualizing threats, and ensuring the long-term viability of a company’s strategic projects. It helps organizations to:
understand attackers’ motives: By examining the motives behind malicious activities, strategic threat intelligence makes it much easier to anticipate their targets and tactics.
assess specific risks affecting a business, sector, or region.
map the threat landscape: Strategic threat intelligence helps build an overall picture of the risks involved.
know how to detect weak signals in the information collected. Weak signals are useful input to strategic threat intelligence, provided you know how to identify and interpret them. They are a way of anticipating an event long before clear signals make it obvious.
“A weak signal is early warning information, of low intensity, that may herald a trend or an important event.” (Igor Ansoff, business strategy consultant, 1970)
identify emerging trends in cyber threats, making it easier to adjust defenses accordingly.
assess the potential impact of geopolitical developments on their cyber risk profile.
optimize and prioritize financial and human resources in internal cybersecurity strategies, based on how the threat directly impacting it evolves, for example.
Let’s imagine you work for a banking organization based in London. Intelligence is telling you that QR code phishing campaigns impersonating financial institutions are on the rise. You’ll therefore need to put more effort into understanding this threat.
Cyber threat intelligence is not a static process. Your goals may change to reflect your company’s priorities and new opportunities or threats. So, it’s important to give yourself enough flexibility to adjust your threat intelligence goals over time and adapt to changes in your environment.
Let’s Recap!
Operational threat intelligence helps security professionals manage the operational side of their organization’s systems and data.
Tactical threat intelligence involves the analysis of threats, associated techniques and tools, and the development of response strategies to strengthen the protection of data and systems within an organization.
Strategic threat intelligence analyzes attacker motives and emerging trends, assesses risks and geopolitical impact, and makes an organization’s security strategies more resilient and effective.
Now that you’ve set your goals, it’s time to define the scope of your cyber threat intelligence.
