It’s November 23, 2014. On the surface, everything is going great for Sony Pictures. Their films are making billions at the box office, and they’re preparing to release many new ones.
Everything was as it should be...or was it?
The next day, on November 24, 2014, a group of hackers identifying themselves as “Guardians of Peace” (GOP) suddenly leaked a veritable treasure trove of the company’s confidential information:
Personal information on employees and their families
Thousands of email exchanges between employees
Films that hadn’t been released yet
And as if that weren’t bad enough, they even erased data from many of Sony’s servers.
It was a huge blow to Sony. Where would you even start with so many disasters striking at the same time? Guardians of Peace’s goal was clear: to cause as much damage as possible. But why?
The Reasons for the Sony Pictures Hack
Like with many cyberattacks, it’s difficult to know for sure who exactly was behind this attack and what their intentions were.
Although there’s no official proof, North Korea was a prime suspect. At the time, Sony Pictures was about to release the film The Interview, which openly mocked the country’s leader Kim Jong-Un. In fact, the plot of the film was Kim Jong-Un being assassinated by a pair of fake journalists.

The Interview’s impending release led to credible fears of terrorist attacks, either on Sony, the movie theaters slated to show the film, or both.
The FBI carried out an investigation in the US, and although North Korea was the likely suspect, no definitive proof was ever found. Thus the mystery of who was behind the attack and why Sony in particular remains...
The Impact of the Sony Cyberattack
The Sony Pictures cyberattack is an interesting case study, as its impact was huge and unprecedented.
The hackers caused significant damage in rendering the servers completely unusable, not to mention the financial impact of films being leaked online before their official release in theaters.
But let’s focus on the publication of confidential information, including Sony’s internal emails. These emails can now be freely accessed on Wikileaks. There are so many emails that there’s even a search engine to make it easier to find exactly what you’d like to read!
If you type in “salary,” you’ll see all emails that mention internal salaries at Sony. You don’t have to look too hard to find the salaries of the company’s highest earners, or find out that certain employees were trying to prevent others from getting a pay raise! Or you can type in “confidential” to access, well, the most confidential information.
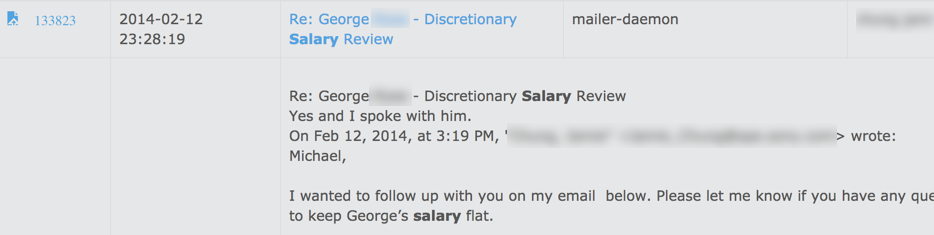
Oh no! Can’t they do something about it? 😱
File a lawsuit? Wipe the emails from the internet?
They’ve already tried to file a lawsuit. And to put a moratorium on media coverage of the whole affair. But it was an impossible task—once emails are out in the wilds of the internet, it’s an impossible task to prevent them from being shared.
Let’s Recap!
Of course, Sony wasn’t properly prepared for a cyberattack. Rumor has it that simple passwords were widely used, among other cybersecurity pitfalls.
But the real lesson to be learned from this is that you can never be fully sure that any conversation is private on the internet. Any data on a device may one day become public—no email, file, or message can be considered truly confidential.
If you really don’t want something to ever become public knowledge, don’t put it online. And if you absolutely must, then use the most powerful encryption system available. Encryption is a form of scrambling messages whose first recorded uses date back to the Roman Empire. Today, we use encryption based on strong mathematical algorithms. When digital data is not encrypted, it is called plaintext. When it has been encrypted, it is called ciphertext. There are two places where your data will need to be encrypted; in transport and at rest.
It doesn’t end there!
Once your email is sent, it sits in the email client-server and can also be accessed there! It is said that this is how the Sony emails were breached. It is also important to ensure that your emails are encrypted while on the server. The protocol responsible for encryption at rest is called Secure Multipurpose Internet Mail Extensions, or S/MIME.
Most email clients such as Gmail, Yahoo, and Outlook have a way to ensure you use TLS and S/MIME to encrypt your data in transport and at rest. There is some add-on software that can be used with your email client as well. For example, open-source software such as GPG is free to use.
GPG is a tool you can use to encrypt your most confidential emails. Of course, there’s a catch: it’s not particularly easy to use for the general public.

But don’t worry! As mentioned, nowadays most email clients have a system to encrypt your emails that integrates easily.
After reading about what happened at Sony, you might think that this only impacts businesses. But what happens when a company storing confidential information on thousands of citizens is hacked? Let’s find out in the next chapter!
